???? Follow Arthur on Twitter: https://x.com/arthurair_es
???? Check out Case Studies: https://bbre.dev/cs
✉️ Sign up for the newsletter: https://bbre.dev/nl
???? Follow me on Twitter: https://bbre.dev/tw
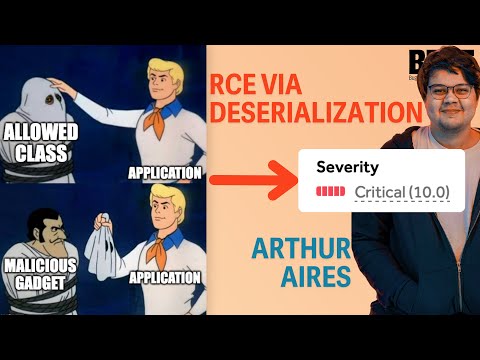
In this video, Arthur Aires shares with us two writeups of RCEs via deserialization, including bypassing a class allowlist and exfiltration of the data via DNS.
???? Get $100 in credits for Digital Ocean: https://bbre.dev/do
Most graphics come from Artur’s talk at OWASP BH (in Portuguese): https://www.youtube.com/watch?v=2-_CEVtirpI
https://github.com/pwntester/SerialKillerBypassGadgetCollection
Timestamps:
00:00 Intro
00:44 Using Burp’s deserialization scanner to discover deserialization
06:06 Bypassing the Lookahead fix by abusing a class from allowlist
12:21 Dealing with SOC and exfiltrating the data via DNS




Add comment